Managed
Advanced security and device management.
All-Inclusive
All security features and full backup of all resources.
The secret of zero trust success
Zero Trust is a modern security strategy we incorporate in our managed modern workplace services. It is based on the principle never trust, always verify, and assume breach. Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network.
Zero Trust Principles
Verify explicitly
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
Use least-privilege access
We limit user access with just-in-time and just-enough-access, risk-based adaptive polices, and data protection to help secure data and improve productivity.
Assume breach
All services are only available from compliant devices that are verified secure, we use analytics to gain visibility into possible malicious behavior and leverage several techniques to scan for threats and possible breaches.
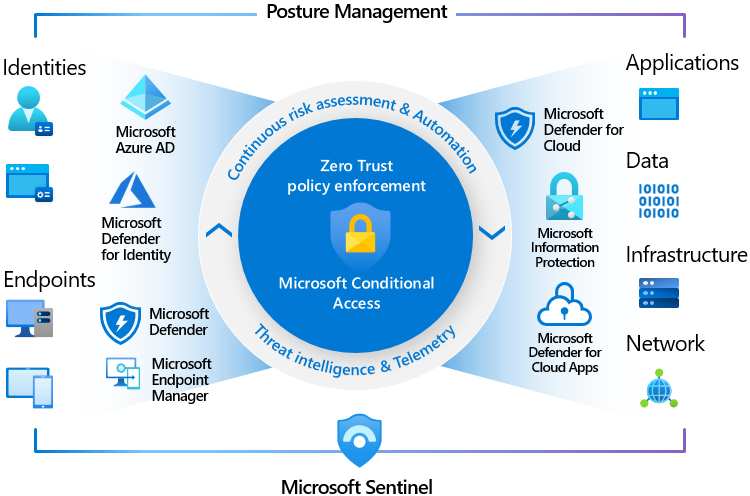
Zero Trust Management
Leveraging our platform, we manage, monitor and proactively remediate issues in your entire environment.
Microsoft 365 management
Leveraging products like Intune and Entra, enriched with our in-house developed applications, we ensure all accounts, virtual, mobile and physical devices are in crisp shape, fully secure and compliant!
This ensures that high-risk, unmanaged computers are prevented from accessing the environment, resulting in a safe and phish-resistant environment.
Application & Vulnerability management
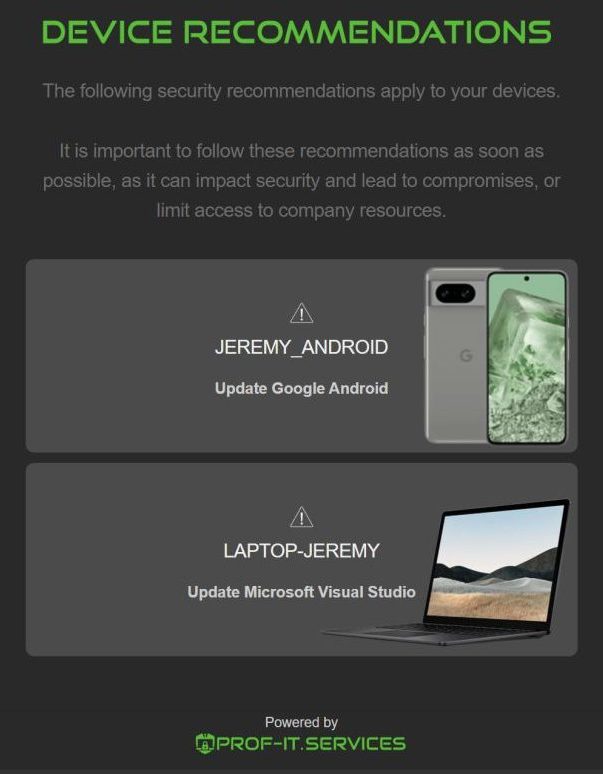
Up-to-date devices and applications are important to prevent breaches, and also increase user experience. Leveraging our in-house developed remediation tool, we ensure that third-party applications are up to date.
We notify users by email and desktop notifications when manual actions are needed, for example for unmanaged Android devices requiring updates.
Managed Microsoft 365 Backup
Backup rules dictate a 3-2-1 backup strategy, 3 copies of all data, stored on 2 different media, and one copy off-site. This ensures business continuity in worst case scenarios.
Our All-Inclusive package includes unlimited backup storage and 99 months retention.
Microsoft 365 phishing protection
Our advanced phishing detection works on any device, for all users, and protects against modern Man In The Middle phishing attacks, which regular MFA does not protect against.
Phish login on the right, confirmed by the red background. This check is performed each time a user signs in, regardless of the device that is used. On the left a demo video of a phish detection.
Dark Web & Security Monitoring
We use several tools and in-house developed applications to monitor and secure every managed environment.
Microsoft Sentinel
We monitor for suspicious Microsoft 365 account activity that could indicate compromises. This includes, for example, Outlook Inbox rule creation, indicating possible invoice fraud scams after user compromises.
Microsoft 365 activity is matched with threat intelligence, containing malicious IP addresses and bot network info.
Security Orchestration Automation and Response
Our in-house developed automation engine isolates users and devices during high-severity incidents. Ensuring threats and threat actors are unable to move lateral throughout the organization or to customers.
Dark Web Monitoring
Continuous 24/7 monitoring of the Dark Web for domains, credentials, IP addresses, and email addresses alerts us to any breaches, indicating compromises in internal or third-party systems. This proactive approach enables us to take action before threat actors can exploit this intelligence.

Azure Virtual Desktop – your computer in the cloud
Work on a virtual desktop, dynamically scalable, pay per used hour
We specialize in Azure Virtual Desktop Environments and can easily manage and deploy a full AVD environment in a short time span. Our Intune environment already contains all best practices and is ready to manage AVD Hosts, eliminating the need for expensive hosted infrastructure.
- Pay only for what you use, auto-scale up and down when users sign in.
-
- Managed with Entra and Intune, leveraging enterprise state roaming, results in an identical copy of your local managed device.
-
- Extremely useful for publishing legacy applications that require a backend server.
- Optional GPUs allow graphical designers to work from anywhere without high-end hardware. Auto-scaling keeps the costs low.

Request our white-paper!
Our managed modern workplace services and platform automation features are not limited to those listed on this webpage. Request our service description white-paper to learn more.
2578 Broadway #579
New York 10025
United States
Paxlaan 10 #9129
2131 PZ, Hoofddorp
The Netherlands
